IPv6 addresses assigned by ISPs are usually not static:
|
|
While the address won’t change during the PPPoE session’s lifespan, ISPs often have mechanisms like timed interruptions and reconnections on their BRAS, leading to changes in our IPv6 address. In newer versions of RouterOS, when the DHCPv6-acquired prefix becomes invalid, the device updates the address “lifetime” to 0, thereby removing the old address. This is a good solution.
However, in this article about optimizing multi-line internet access using BGP full tables on RouterOS, it’s mentioned:
although v6 achieves traffic diversion through these methods, there are still issues because there is no NAT and devices cannot intelligently choose which prefix of the IP address to use.
So, having a stable prefix alone isn’t sufficient; we need the device’s firewall to “intelligently” update the outgoing IPv6 source address to the one we want it to use. This is crucial to achieve optimal results for multi-ISP optimization. To achieve this goal, we can use the NETMAP target provided by netfilter.
Let’s assume our router has the following prefixes:
- From China Telecom: 240e:388:6501:ab00::/56
- From China Mobile: 2409:8a1e:6a64:2XX0::/60
- Self-announced: 2602:feda:de0:700::/56
We’re selecting a fixed address range with the smallest prefix for translation, which is 2602:feda:de0:700::/60.
Notice
If you don’t have your own prefix, you can configure IPv6 SLAAC using IPv6 ULA addresses, for example,
fd34:38a:f295:a00::/64.
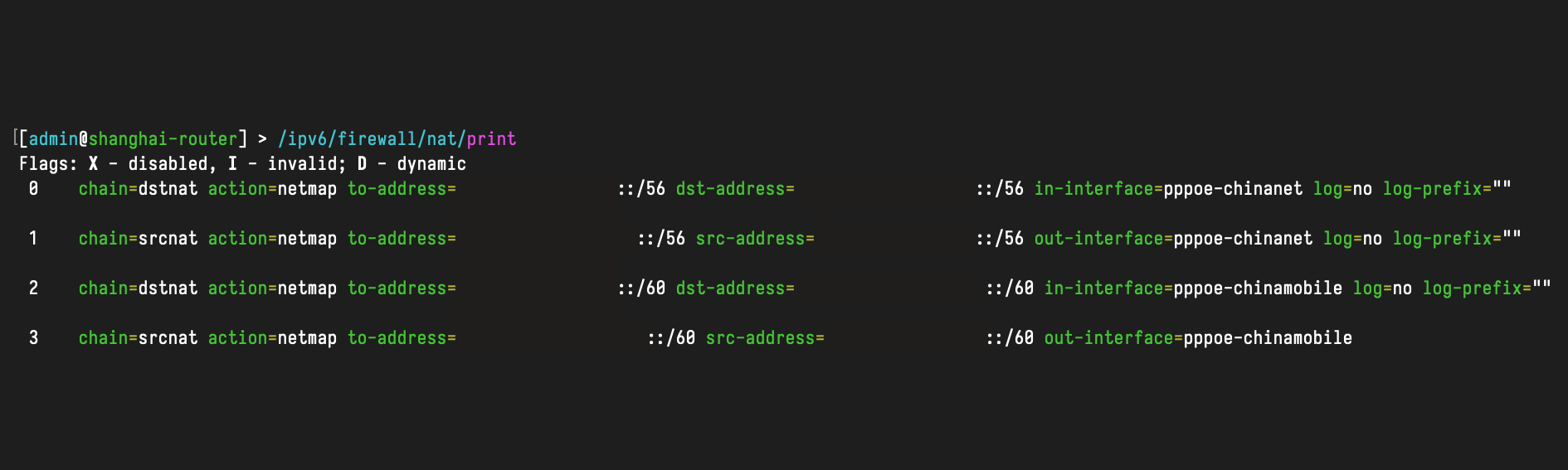
For outgoing connections to the pppoe-chinanet interface, where the source address is within the range of 2602:feda:de0:700::/60, we’ll use the firewall to map the source address to the range of 240e:388:6501:ab00::/60 (which is China Telecom’s address range):
|
|
Of course, we can’t just handle outbound traffic and ignore incoming traffic. Otherwise, when responses from external services reach the router and it realizes there’s no directly adjacent address using the 240e:388:6501:ab00::/60 prefix, we need to handle the return traffic:
|
|
Similarly, rules for China Mobile can be written as follows:
|
|
Finally, we also need to add an update script to the corresponding DHCPv6 configuration to update the firewall rules, using China Mobile’s client as an example:
|
|
That’s it!
We can pick an IPv6 address and try a traceroute:
|
|
As we can see, when this NAS accesses Cloudflare, it uses its my own prefix. When accessing domestic addresses, it actually uses China Telecom’s prefix.